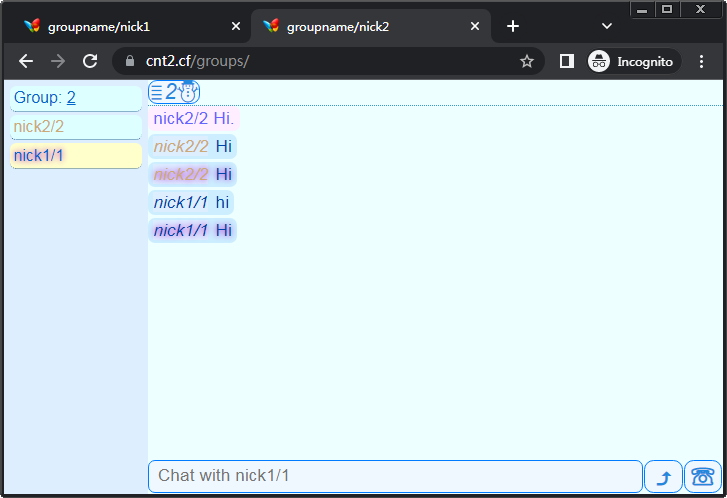
1
HFS ~ HTTP File Server / Re: Warning: HFS v2.x has a severe vulnerability
« Last post by LeoNeeson on Today at 06:46:05 AM »that's great, congratulations with your achievement, Leo!Thanks, it means a lot that you like it, I appreciate it.
 To me, it's like an exercise to dip my toes on Delphi, although there is still a long way to go...
To me, it's like an exercise to dip my toes on Delphi, although there is still a long way to go...you prefer 2.3 over 2.4 ?Not really, some parts of it only (2.4 has huge improvements), but mainly I'm using 2.3 in my tests because it is much easier for me to build it (using TD2006). And since it was the latest stable version published, it was the version I've used it as example.
Is the url the only way to use the vulnerability? Even if the POC of the CVE uses the url, be sure to consider the possibility of the attack coming from a header.Yes, I know what you mean ('Host' header is not covered, for example), that's why I'm not completely happy with my 'single line' fix (although it works). That's why I'm testing a completely new fix (instead the previous code). See...
» Alternative method to stop this macro vulnerability:
Add the line marked in green, after line 5084 in 'main.pas' (v2.3m)
Quote
runEventScript('pre-filter-request');
// Check macro leaks, prevent hack attempts
if anyMacroMarkerIn(conn.request.full) then
begin
data.disconnectReason:='Hack attempt blocked. This event has been logged!';
add2log('Hack attempt blocked: '+ansiToUTF8(conn.request.url));
getPage('deny', data);
conn.reply.mode:=HRM_BAD_REQUEST;
exit;
end;
It works, but even then, it's just a simple check and stop, not a true 'urlvar' filtering (and I can't be 100% sure if it is enough or if some hacker could think a workaround to bypass this measure). And if the browser asks for the 'favicon.ico' along with the same request, it gets logged as hack attempt too (and I don't like this, and I have to think how to handle it, perhaps with 'urlCmd'). Alternatively, I was thinking of doing a 'stringReplace' of macro markers on 'request.full' at an earlier stage, right on the 'handleHeaderData' procedure (which also works, as second measure), but I don't like this approach, since it could mess with other parts of the code.
Well, I think that's all I will be working with this at the moment, I don't have too much time to go deeper analyzing this, it's only a start for now.
 Recent Posts
Recent Posts